Double security!
Enforce length in database and then through the front end by validating in this case password values (PHPRunner example).
First the backend
You have a nvarchar(128) column in MS Azure SQL Database (or any Microsoft SQL Server database) and you wish to add a check constraint that does not allow a value in the column to be less than lets say 15 characters long.
tablename = users
field = userpassword
ALTER TABLE dbo.users
ADD CONSTRAINT [MinLengthConstraint]
CHECK (DATALENGTH([userpassword]))>14;
And then a good way to check the constraints on an individual table using TSQL through SSMS for MS AZURE.
SELECT TABLE_NAME,
CONSTRAINT_TYPE,
CONSTRAINT_NAME
FROM INFORMATION_SCHEMA.TABLE_CONSTRAINTS
WHERE TABLE_NAME ='users';
Front End
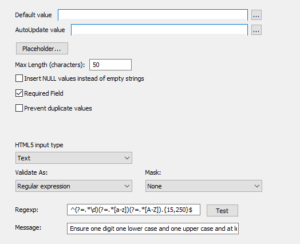
Now for double security in your web application use a regular expression to prevent users entering a weak password.
^(?=.*\d)(?=.*[a-z])(?=.*[A-Z]).{15,128}$
^ # start of the string
(?=.*\d) # a digit must occur at least once
(?=.*[a-z]) # a lower case letter must occur at least once
(?=.*[A-Z]) # an upper case letter must occur at least once
.{15,128} # 15-128 character password must be a minimum of 15 characters and a maximum of 128
$ # end of the string
OWASP – Open Web Application Security Project


